サーバ証明書の確認
サーバ証明書(cert.pem)を確認する際は、下記のようにコマンドを実行します。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
% openssl x509 -in /etc/letsencrypt/live/negix.org/cert.pem -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
04:53:cf:68:60:97:47:e4:7a:8b:34:60:a6:0c:7c:cf:85:47
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = US, O = Let's Encrypt, CN = R3
Validity
Not Before: Jan 26 01:00:06 2023 GMT
Not After : Apr 26 01:00:05 2023 GMT
Subject: CN = negix.org
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (384 bit)
pub:
04:e6:1b:ab:e0:a3:ee:f7:74:55:42:97:21:10:ae:
97:01:6e:4d:6f:cd:8b:3f:f3:fd:51:76:ec:f2:39:
79:c8:a3:e4:6b:e0:99:3d:25:20:d2:2d:09:42:d8:
25:e5:a9:36:41:34:ae:a3:7d:67:cf:a7:74:75:c7:
85:7c:62:ad:c1:a2:d0:03:1b:28:80:0a:ea:d4:ec:
3d:76:ae:63:95:a6:d3:3a:2f:15:4c:bb:b4:ac:ed:
e0:3f:72:02:ad:c3:c3
ASN1 OID: secp384r1
NIST CURVE: P-384
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Subject Key Identifier:
5E:BC:D0:1E:67:D7:7D:32:95:C4:60:7B:F6:59:E9:8C:2E:E3:1D:73
X509v3 Authority Key Identifier:
14:2E:B3:17:B7:58:56:CB:AE:50:09:40:E6:1F:AF:9D:8B:14:C2:C6
Authority Information Access:
OCSP - URI:http://r3.o.lencr.org
CA Issuers - URI:http://r3.i.lencr.org/
X509v3 Subject Alternative Name:
DNS:*.negix.org, DNS:negix.org
X509v3 Certificate Policies:
Policy: 2.23.140.1.2.1
Policy: 1.3.6.1.4.1.44947.1.1.1
CPS: http://cps.letsencrypt.org
CT Precertificate SCTs:
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : B7:3E:FB:24:DF:9C:4D:BA:75:F2:39:C5:BA:58:F4:6C:
5D:FC:42:CF:7A:9F:35:C4:9E:1D:09:81:25:ED:B4:99
Timestamp : Jan 26 02:00:07.120 2023 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:44:02:20:24:CA:CE:EC:D0:4F:64:6A:B6:FC:67:1E:
35:F6:36:9D:42:A1:7E:35:83:22:D1:21:8C:C6:07:AD:
B4:37:F6:12:02:20:44:D2:A2:88:08:E5:F1:CA:39:A8:
1B:6D:92:80:44:38:47:6A:21:54:70:13:C4:F2:B5:AA:
8C:0A:1D:28:EF:E4
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : E8:3E:D0:DA:3E:F5:06:35:32:E7:57:28:BC:89:6B:C9:
03:D3:CB:D1:11:6B:EC:EB:69:E1:77:7D:6D:06:BD:6E
Timestamp : Jan 26 02:00:07.110 2023 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:46:02:21:00:DF:29:A3:6A:1D:DF:8C:2B:C2:73:FC:
29:9A:93:FA:85:DD:E9:81:84:DB:5D:C0:48:89:0E:25:
7A:1C:FB:AB:06:02:21:00:A5:32:15:AC:D3:BF:65:FE:
8F:3F:85:E2:8A:6C:B5:56:D8:06:F7:57:EA:77:08:A2:
1F:94:DB:18:63:57:9A:27
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
11:fb:9e:95:7b:08:cf:1f:fa:c4:86:f1:01:6c:e0:38:b8:95:
94:63:8f:b2:9f:67:e5:fc:28:60:aa:0a:fd:4b:8c:ea:6d:03:
34:ca:d1:63:94:f0:d8:8d:9c:37:97:0f:8b:a8:c6:46:5d:27:
c7:1b:f4:fb:2f:ab:66:70:81:ee:76:da:67:1f:60:91:ca:5b:
da:80:89:2b:d1:65:c4:95:a3:70:b7:0f:03:40:a5:32:84:46:
17:6f:9b:2d:24:ff:af:df:e3:71:05:c9:a8:9e:e9:cc:b3:60:
57:24:bb:3f:d4:3b:66:82:c5:54:28:dc:d4:c2:f4:03:b2:da:
91:81:ab:f6:2c:78:e7:cb:6e:0b:1d:91:9a:c7:31:f3:d8:ef:
bc:f1:fe:02:40:77:b2:0c:75:ea:ab:f9:9f:ed:c5:ce:85:74:
cb:a3:c0:d5:b3:88:11:87:5a:b3:6f:b2:b3:29:14:12:84:c8:
5f:84:a7:cf:53:b8:64:81:e6:29:49:7a:de:2b:1f:3f:e7:89:
40:b7:74:96:7b:a1:cd:93:2a:5c:6b:e6:66:a6:05:7e:29:47:
81:e7:9b:73:2e:df:ba:b3:fa:26:93:4e:3d:bf:e6:38:28:f7:
16:53:d5:97:95:f3:83:fc:be:3d:d6:64:92:63:cb:38:53:1d:
de:71:f2:0f
fullchain.pem内の証明書を全て確認したい時は、下記のようにコマンドを実行します。
1
% openssl crl2pkcs7 -nocrl -certfile /etc/letsencrypt/live/negix.org/fullchain.pem | openssl pkcs7 -print_certs -text -noout
証明書の検証
証明書を検証する際は、openssl verifyコマンドを用います。
ルート証明書と中間証明書を-CAfileオプションで渡す必要がある点に注意が必要です。
1
2
3
4
5
6
7
% cd /etc/letsencrypt/live/negix.org
% openssl verify -show_chain -CAfile <(cat /etc/ssl/certs/ISRG_Root_X1.pem chain.pem) cert.pem
cert.pem: OK
Chain:
depth=0: CN = negix.org (untrusted)
depth=1: C = US, O = Let's Encrypt, CN = R3
depth=2: C = US, O = Internet Security Research Group, CN = ISRG Root X1
秘密鍵の確認
サーバ証明書内の公開鍵の対となる秘密鍵はprivkey.pemです。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
% sudo openssl pkey -in live/negix.org/privkey.pem -text -noout
Private-Key: (384 bit)
priv:
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:
xx:xx:xx
pub:
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:
xx:xx:xx:xx:xx:xx:xx
ASN1 OID: secp384r1
NIST CURVE: P-384
【おまけ】 CSRの確認
認証局に証明書の発行を要求する際に用いられるCSR(Certificate Signing Request)は、
certbotにより/etc/letsencrypt/csrディレクトリ以下に自動的に生成され、Let’s Encryptに送信されています。
これを確認したい時は、下記のようにopenssl reqを用います。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
% openssl req -in /etc/letsencrypt/csr/0000_csr-certbot.pem -noout -text
Certificate Request:
Data:
Version: 1 (0x0)
Subject:
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (384 bit)
pub:
04:e6:1b:ab:e0:a3:ee:f7:74:55:42:97:21:10:ae:
97:01:6e:4d:6f:cd:8b:3f:f3:fd:51:76:ec:f2:39:
79:c8:a3:e4:6b:e0:99:3d:25:20:d2:2d:09:42:d8:
25:e5:a9:36:41:34:ae:a3:7d:67:cf:a7:74:75:c7:
85:7c:62:ad:c1:a2:d0:03:1b:28:80:0a:ea:d4:ec:
3d:76:ae:63:95:a6:d3:3a:2f:15:4c:bb:b4:ac:ed:
e0:3f:72:02:ad:c3:c3
ASN1 OID: secp384r1
NIST CURVE: P-384
Attributes:
Requested Extensions:
X509v3 Subject Alternative Name:
DNS:negix.org, DNS:*.negix.org
Signature Algorithm: ecdsa-with-SHA256
Signature Value:
30:65:02:30:24:9a:38:27:01:7e:c7:58:0c:a3:99:e4:b2:dc:
4d:22:4f:96:3f:0f:90:5c:7d:8b:0e:cf:eb:ab:ee:64:6e:11:
73:74:d4:f2:cf:ce:16:d1:77:0c:81:96:fe:70:ae:82:02:31:
00:ae:47:60:4f:a9:d6:74:b2:38:8c:5b:f3:46:65:61:02:92:
a2:52:79:6b:c3:1a:ab:4a:28:71:b1:92:41:f1:07:ca:20:a7:
62:1f:e6:e1:5e:d9:ce:5f:14:15:82:1a:51
NGINXの設定
mozilla - SSL Configration Generatorで生成した設定ファイルを参考に、Webサーバ(NGINX)を設定します。
/etc/nginx/conf.d/negix.org.conf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
server {
listen 160.251.76.38:80;
server_name negix.org, www.negix.org;
location / {
return 301 https://negix.org$request_uri;
}
}
server {
listen 160.251.76.38:443 ssl http2 default;
server_name negix.org, www.negix.org;
ssl_certificate /etc/letsencrypt/live/negix.org/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/negix.org/privkey.pem;
# ssl_dhparam /etc/nginx/dhparam.pem;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:10m;
ssl_session_tickets off;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384;
ssl_prefer_server_ciphers off;
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/letsencrypt/live/negix.org/chain.pem;
add_header Strict-Transport-Security 'max-age=31536000; includeSubDomains;';
add_header X-Frame-Options SAMEORIGIN;
add_header X-XSS-Protection "1; mode=block";
add_header X-Content-Type-Options nosniff;
location / {
root /usr/share/nginx/html;
index index.html index.htm;
}
}
設定できたらnginxを起動しましょう。
1
% sudo systemctl enable --now nginx
OCSP Staplingの確認
1
2
3
4
5
6
7
8
9
10
11
12
% echo QUIT | openssl s_client -connect negix.org:443 -status | grep -i OCSP
depth=2 C = US, O = Internet Security Research Group, CN = ISRG Root X1
verify return:1
depth=1 C = US, O = Let's Encrypt, CN = R3
verify return:1
depth=0 CN = negix.org
verify return:1
DONE
OCSP response:
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
SSL Server Testの実施
最後にQualys社が提供しているSSL Server Testを、Webサーバに対して実施します。
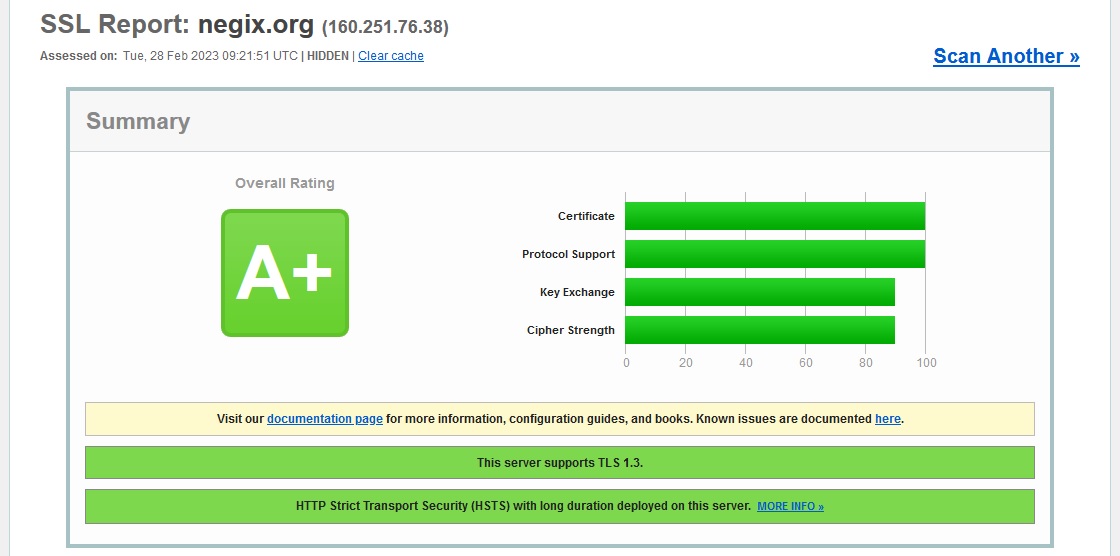
無事A+評価を得ることができました。